Protection
Introduction
Protection: a general term for all the mechanisms which control the access of a program to other things in the system.
What is the Main goal of the paper?
- Objects
- things in the system need to be protected
- domains, files, segments, terminals
- unique name( key attribute of an object)
- Domains
- entities which have access to objects
- executing environment ⇒ object
- access matrix
- A(i, j) = A(domain name, object name) = list of access attribute
- copy flag: controls the transfer of access
Mechanism VS policy
- Mechanism: primitives needed by build a operating system
- Policy: particular strategy used for scheduling, allocating memory, organizing files
Abstraction
What is an object?
- the things in the system which have to be protected, processes, domains, files, segments and terminals.
- In HYDRA:
- 3 object types: procedure(code +data), LNS(local name space, execution environment, domain), process(线程?)
- capability: consists of a reference to an object together with a collection of "access rights" to the objects
- Each capability includes information detailing the operations which may be performed on the objects referenced by the capability. (right list)
- In Mulltics: objects == segments
- Are domain objects have to be protected?
- Yes.
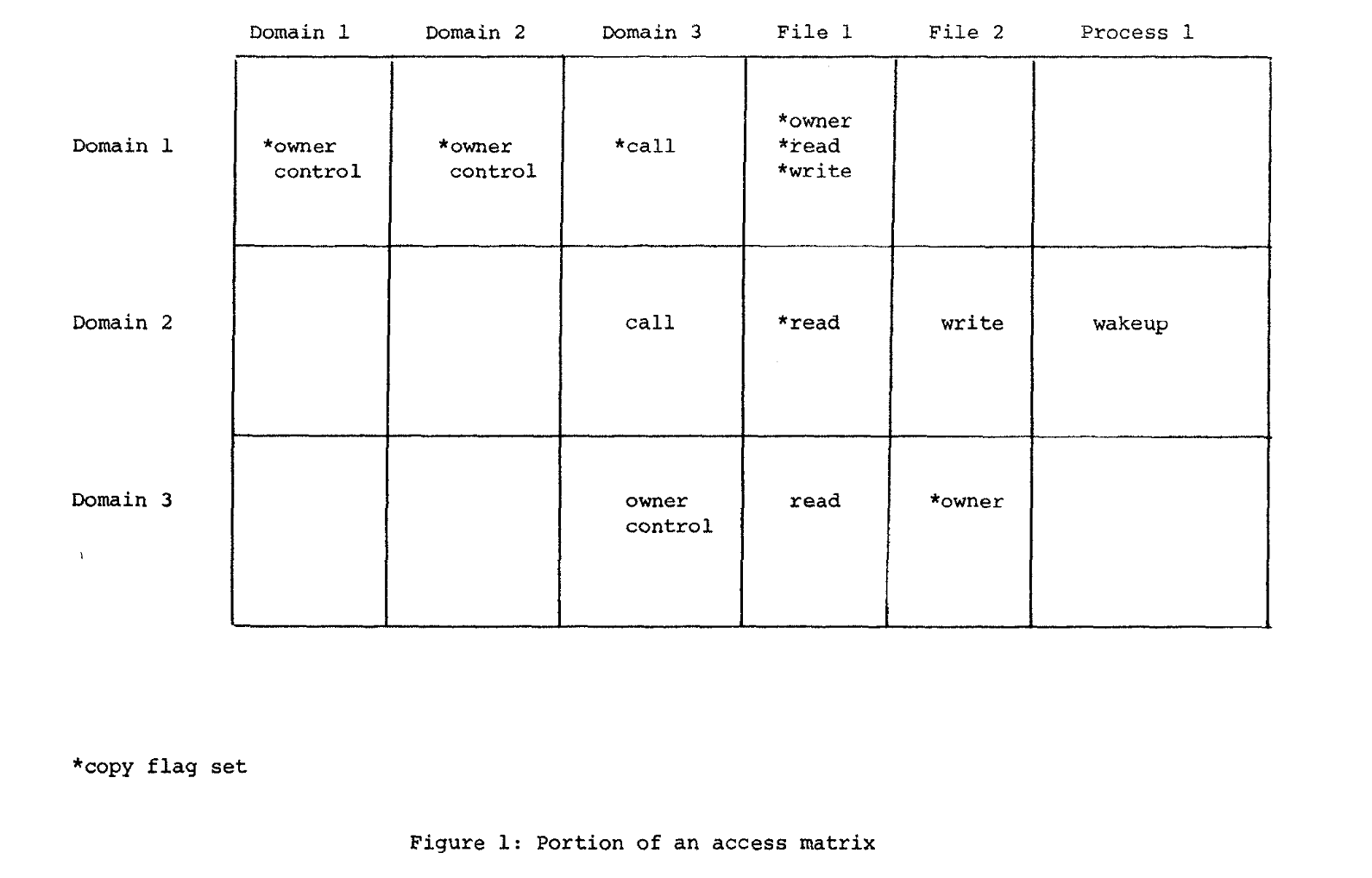
What is an access matrix?
- rows are labeled by domain names.
- columns by objects names (so, also could be domain names).
- owner: relationship between domain <==> object, d1 owns x, d1 could add attr to A[d_i, x]; can not take away access copy: domain<==> object, d1 have copy flag of x, d1 could copy rights to A[d_i, x] control: domain<==>domain, d1 have control over d2, d1 could remove attributes from row1 and row 2 owner v.s. copy: _add _any attribute v.s. only copy rights of myself to others owner v.s. control: <domain, file> v.s. < domain, domain>
Implementation
- The access matrix is sparse, it is not practical to store the entire matrix.
Two approaches
- Capability method - Attach the d'th row of access matrix A to the domain d. Domain is defined by capability list, C-list.(info on domain)
- capability domain d = <x1:A[d, x]> <x2:A[d,x2]>
- domain is defined by a C-list
- Access Control List (ACL) method - Attach the protection information to the object rather than the domain.(info on object)
- objects have <key value, access attributes> pairs
- Easier to revoke access
- Likely to be more expensive
- A hybrid version, an object can be accessed by access key to obtain a capability, which is then used for subsequent accesses. This process when applied to files is open a file -> file descriptor.